January 5, 2022 | Digital Marketing, Intelligent Security

Identity and Access management basically is a framework of policies and technologies made to ensure the right users have appropriate information and access to technology resources.
Identity management is related to authenticating users, while Access management is related to authorized users.
There has been increasing pressure on IT departments to protect Access to corporate resources. And thus, relying on manual and error-prone processes is no longer an option for assigning and tracking user privileges. IAM automates these tasks and facilitates granular access control and auditing of all corporate assets on-premises and in the cloud.
IAM has an ever-increasing list of features like biometrics, behavior analytics, and AI, and these all are well suited to the demands of the new security landscape. For example, IAM’s tight control of resource access in highly distributed and dynamic environments aligns with the industry’s transition from firewalls to zero-trust models and with the security requirements of IoT.
IT companies have this notion that IAM is for large-size companies with big budgets, but this technology, in reality, is accessible for all company sizes.
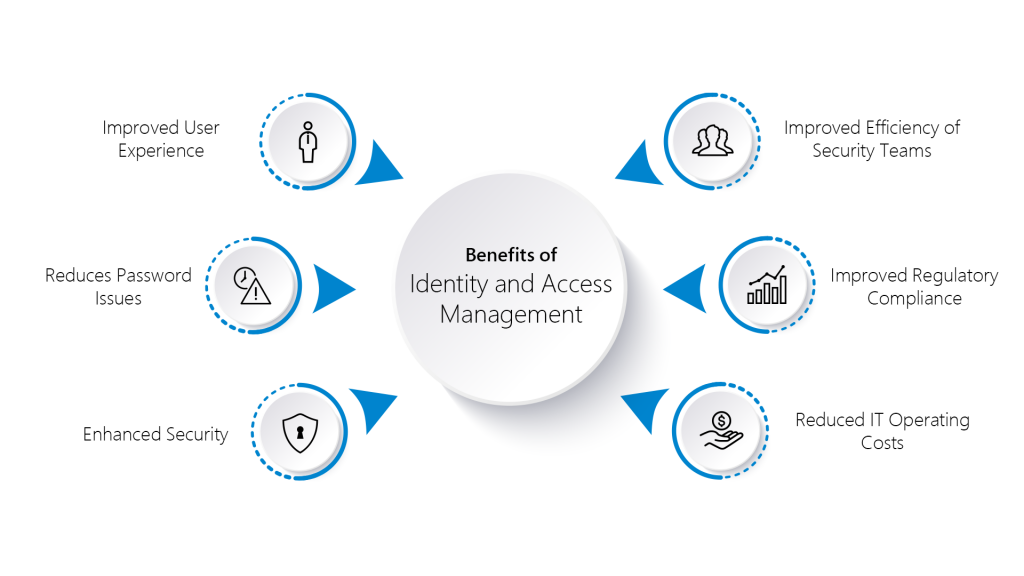
For initiation, capturing, recording, and managing user IDs and their related access permissions in an automated manner, IAM technologies can be used. Following are the benefits of IAM to the organization:
Companies gain a competitive advantage by implementing IAM tools and following its related best practices.
The foundation of most organizations begins with on-premises Active Directory (AD) forest. Microsoft offers several add-on features in Azure Active Directory Premium (AADP), which can be used to further secure Access to MS Azure and even other cloud providers.
User identities in every organization in Azure Active Directory (AAD) begin on-premises in a traditional AD forest. Chances of being an active account on-premises also being active in AAD are high. And so goes with compromise.
Identities used to manage Microsoft Azure must be treated like any other identity, like separating accounts from day-to-day login. And must be secured with storing password policies and two-factor authentication.
Strong in premises foundation helps extend additional security privileged identities in Microsoft Azure with AADP. It offers a multitude of features and capabilities. Conditional Access allows users to authenticate different applications.
At the least use of conditional Access is used to require multi-factor authentication anytime Access is given to the portal. Additional criteria like known devices or known networks can also be added here. These policies are easy to implement and a great way of security of data and organization.
Using the AADP plan, adding additional security by exploiting the Privileged Identity Management (PIM) becomes easy. PIM removers permanent administrative arrives.
These controls are adding security by limiting Access to defined time. And to keep a trail of what is up and if something goes wrong is possible due to.
If upgrading to AAD is a concern, PIM addition will bring great news.
Another exceptional feature of AADP P2 is access reviews. The functionality lets you carry on a frequent re-attestation campaign for empowered designation as well as any group in AAD. Access reviews are designed in such a way that it incorporates an amiable user interface in the AAD access panel.
You can easily synchronize the reviews to bring automation on a uniform basis for a given role. For instance, the frequency of the owner role and reader role might vary from each other. One may be evaluated quarterly, and one can be evaluated annually. On the basis of the defined schedule, you can determine the system where an automated Email reminder would be sent for the reviewers. Once the reviewers start working, AAD can be configured to automated revoke access for any users who the reviewers determine no longer require Access. On top of that, captivating the expansion of Access also facilitates compliance behavior by providing a user-friendly and budget certification/attestation system.
atQor is one of the leading IAM solution providers in the market. We have been providing solutions and services for IAM for a long time now. We have experts who are Identity and Access Management services Providers for a long time and have gained massive experience for the same. We customize solutions and services on the basis of the company’s needs and requirements. And thus facilitate the organization to help secure their environment and data exchanges.